# T1005 (/docs/T1005)
## Description from ATT\&CK
Adversaries may search local system sources, such as file systems, configuration files, local databases, virtual machine files, or process memory, to find files of interest and sensitive data prior to Exfiltration.
Adversaries may do this using a [Command and Scripting Interpreter](https://attack.mitre.org/techniques/T1059), such as [cmd](https://attack.mitre.org/software/S0106) as well as a [Network Device CLI](https://attack.mitre.org/techniques/T1059/008), which have functionality to interact with the file system to gather information.(Citation: show\_run\_config\_cmd\_cisco) Adversaries may also use [Automated Collection](https://attack.mitre.org/techniques/T1119) on the local system.
## Tests
### Test #1 - Copy Apple Notes database
This command will copy Apple Notes database files using AppleScript as seen in Atomic Stealer.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| ----------------- | ---- | ------------- |
| destination\_path | str | `/tmp` |
tracert, and GET requests to websites, or performing initial speed testing to confirm bandwidth.
Adversaries may use the results and responses from these requests to determine if the system is capable of communicating with their C2 servers before attempting to connect to them. The results may also be used to identify routes, redirectors, and proxy servers.
## Tests
### Test #1 - Test Internet connection
Adversaries may check for Internet connectivity on compromised systems.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| -------- | ---- | ------------------------ |
| testURL | str | `https://www.google.com` |
net view using [Net](https://attack.mitre.org/software/S0039), or, on ESXi servers, `esxcli network diag ping`.
Adversaries may also analyze data from local host files (ex: C:\Windows\System32\Drivers\etc\hosts or /etc/hosts) or other passive means (such as local [Arp](https://attack.mitre.org/software/S0099) cache entries) in order to discover the presence of remote systems in an environment.
Adversaries may also target discovery of network infrastructure as well as leverage [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) commands on network devices to gather detailed information about systems within a network (e.g. show cdp neighbors, show arp).(Citation: US-CERT-TA18-106A)(Citation: CISA AR21-126A FIVEHANDS May 2021)
## Tests
### Test #1 - Read local hosts file
Adversaries may analyze data from local host file (/etc/hosts)
whoami. In macOS and Linux, the currently logged in user can be identified with w and who. On macOS the dscl . list /Users | grep -v '\_' command can also be used to enumerate user accounts. Environment variables, such as %USERNAME% and $USER, may also be used to access this information.
On network devices, [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) commands such as `show users` and `show ssh` can be used to display users currently logged into the device.(Citation: show\_ssh\_users\_cmd\_cisco)(Citation: US-CERT TA18-106A Network Infrastructure Devices 2018)
## Tests
### Test #1 - Get user (using System Info)
Retrieves the current user's short and long names using the system info command.
Get-Process via [PowerShell](https://attack.mitre.org/techniques/T1059/001). Information about processes can also be extracted from the output of [Native API](https://attack.mitre.org/techniques/T1106) calls such as CreateToolhelp32Snapshot. In Mac and Linux, this is accomplished with the ps command. Adversaries may also opt to enumerate processes via `/proc`. ESXi also supports use of the `ps` command, as well as `esxcli system process list`.(Citation: Sygnia ESXi Ransomware 2025)(Citation: Crowdstrike Hypervisor Jackpotting Pt 2 2021)
On network devices, [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) commands such as `show processes` can be used to display current running processes.(Citation: US-CERT-TA18-106A)(Citation: show\_processes\_cisco\_cmd)
## Tests
### Test #1 - Get all processes
Retrieves a list of all running processes on the system using System Events. This provides comprehensive process enumeration capabilities and may require TCC approval for System Events access.
⚠️ TCC Required
osascript /path/to/script or osascript -e "script here". Aside from the command line, scripts can be executed in numerous ways including Mail rules, Calendar.app alarms, and Automator workflows. AppleScripts can also be executed as plain text shell scripts by adding #!/usr/bin/osascript to the start of the script file.(Citation: SentinelOne AppleScript)
AppleScripts do not need to call osascript to execute. However, they may be executed from within mach-O binaries by using the macOS [Native API](https://attack.mitre.org/techniques/T1106)s NSAppleScript or OSAScript, both of which execute code independent of the /usr/bin/osascript command line utility.
Adversaries may abuse AppleScript to execute various behaviors, such as interacting with an open SSH connection, moving to remote machines, and even presenting users with fake dialog boxes. These events cannot start applications remotely (they can start them locally), but they can interact with applications if they're already running remotely. On macOS 10.10 Yosemite and higher, AppleScript has the ability to execute [Native API](https://attack.mitre.org/techniques/T1106)s, which otherwise would require compilation and execution in a mach-O binary file format.(Citation: SentinelOne macOS Red Team) Since this is a scripting language, it can be used to launch more common techniques as well such as a reverse shell via [Python](https://attack.mitre.org/techniques/T1059/006).(Citation: Macro Malware Targets Macs)
## Tests
### Test #1 - Open application
Opens an application on the system. The application will be in focus after running the command.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| --------------- | ---- | ------------- |
| applicationName | str | `Finder` |
/var/log/ directory. Subfolders in this directory categorize logs by their related functions, such as:(Citation: Linux Logs)
* /var/log/messages:: General and system-related messages
* /var/log/secure or /var/log/auth.log: Authentication logs
* /var/log/utmp or /var/log/wtmp: Login records
* /var/log/kern.log: Kernel logs
* /var/log/cron.log: Crond logs
* /var/log/maillog: Mail server logs
* /var/log/httpd/: Web server access and error logs
## Tests
### Test #1 - Delete system log files
This test deletes the system log file using Finder application.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| -------- | ---- | --------------------- |
| logPath | str | `/var/log/system.log` |
systemsetup configuration tool on macOS. Adversaries may leverage a [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) on network devices to gather detailed system information (e.g. show version).(Citation: US-CERT-TA18-106A) On ESXi servers, threat actors may gather system information from various esxcli utilities, such as `system hostname get` and `system version get`.(Citation: Crowdstrike Hypervisor Jackpotting Pt 2 2021)(Citation: Varonis)
Infrastructure as a Service (IaaS) cloud providers such as AWS, GCP, and Azure allow access to instance and virtual machine information via APIs. Successful authenticated API calls can return data such as the operating system platform and status of a particular instance or the model view of a virtual machine.(Citation: Amazon Describe Instance)(Citation: Google Instances Resource)(Citation: Microsoft Virutal Machine API)
[System Information Discovery](https://attack.mitre.org/techniques/T1082) combined with information gathered from other forms of discovery and reconnaissance can drive payload development and concealment.(Citation: OSX.FairyTale)(Citation: 20 macOS Common Tools and Techniques)
## Tests
### Test #1 - Get system information
Retrieves comprehensive system information including OS version, hardware details, and system configuration using the system info command. This provides detailed system reconnaissance capabilities without requiring elevated privileges.
dir, tree, ls, find, and locate.(Citation: Windows Commands JPCERT) Custom tools may also be used to gather file and directory information and interact with the [Native API](https://attack.mitre.org/techniques/T1106). Adversaries may also leverage a [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) on network devices to gather file and directory information (e.g. dir, show flash, and/or nvram).(Citation: US-CERT-TA18-106A)
Some files and directories may require elevated or specific user permissions to access.
## Tests
### Test #1 - Copy files from desktop
FileGrabber grabs files from desktop and copies them to a temporary folder
**Input Arguments:**
| Argument | Type | Default Value |
| --------------- | ---- | ------------------ |
| destinationPath | str | `/tmp/FileGrabber` |
net user and net localgroup of the [Net](https://attack.mitre.org/software/S0039) utility and id and groups on macOS and Linux can list local users and groups.(Citation: Mandiant APT1)(Citation: id man page)(Citation: groups man page) On Linux, local users can also be enumerated through the use of the /etc/passwd file. On macOS, the dscl . list /Users command can be used to enumerate local accounts. On ESXi servers, the `esxcli system account list` command can list local user accounts.(Citation: Crowdstrike Hypervisor Jackpotting Pt 2 2021)
## Tests
### Test #1 - Enumerate Local Accounts
Adversaries may attempt to get a listing of local system accounts.
⚠️ TCC Required
CopyFromScreen, xwd, or screencapture.(Citation: CopyFromScreen .NET)(Citation: Antiquated Mac Malware)
## Tests
### Test #1 - Take screenshot
Capture screenshot using System Events
⚠️ TCC Required
clip.exe or Get-Clipboard.(Citation: MSDN Clipboard)(Citation: clip\_win\_server)(Citation: CISA\_AA21\_200B) Additionally, adversaries may monitor then replace users’ clipboard with their data (e.g., [Transmitted Data Manipulation](https://attack.mitre.org/techniques/T1565/002)).(Citation: mining\_ruby\_reversinglabs)
macOS and Linux also have commands, such as pbpaste, to grab clipboard contents.(Citation: Operating with EmPyre)
## Tests
### Test #1 - Get clipboard content (using System Events)
Retrieves the current clipboard content using System Events.
⚠️ TCC Required
systemsetup on macOS.(Citation: MSDN System Time)(Citation: Technet Windows Time Service)(Citation: systemsetup mac time) These time settings may also be synchronized between systems and services in an enterprise network, typically accomplished with a network time server within a domain.(Citation: Mac Time Sync)(Citation: linux system time)
System time information may be gathered in a number of ways, such as with [Net](https://attack.mitre.org/software/S0039) on Windows by performing net time \hostname to gather the system time on a remote system. The victim's time zone may also be inferred from the current system time or gathered by using w32tm /tz.(Citation: Technet Windows Time Service) In addition, adversaries can discover device uptime through functions such as GetTickCount() to determine how long it has been since the system booted up.(Citation: Virtualization/Sandbox Evasion)
On network devices, [Network Device CLI](https://attack.mitre.org/techniques/T1059/008) commands such as `show clock detail` can be used to see the current time configuration.(Citation: show\_clock\_detail\_cisco\_cmd) On ESXi servers, `esxcli system clock get` can be used for the same purpose.
In addition, system calls – such as time() – have been used to collect the current time on Linux devices.(Citation: MAGNET GOBLIN) On macOS systems, adversaries may use commands such as systemsetup -gettimezone or timeIntervalSinceNow to gather current time zone information or current date and time.(Citation: System Information Discovery Technique)(Citation: ESET DazzleSpy Jan 2022)
This information could be useful for performing other techniques, such as executing a file with a [Scheduled Task/Job](https://attack.mitre.org/techniques/T1053)(Citation: RSA EU12 They're Inside), or to discover locality information based on time zone to assist in victim targeting (i.e. [System Location Discovery](https://attack.mitre.org/techniques/T1614)). Adversaries may also use knowledge of system time as part of a time bomb, or delaying execution until a specified date/time.(Citation: AnyRun TimeBomb)
## Tests
### Test #1 - Get System Time
An adversary may gather the system time and/or time zone settings from a local or remote system.
⚠️ TCC Required
MSExchangeIS, which will make Exchange content inaccessible.(Citation: Novetta Blockbuster) In some cases, adversaries may stop or disable many or all services to render systems unusable.(Citation: Talos Olympic Destroyer 2018) Services or processes may not allow for modification of their data stores while running. Adversaries may stop services or processes in order to conduct [Data Destruction](https://attack.mitre.org/techniques/T1485) or [Data Encrypted for Impact](https://attack.mitre.org/techniques/T1486) on the data stores of services like Exchange and SQL Server, or on virtual machines hosted on ESXi infrastructure.(Citation: SecureWorks WannaCry Analysis)(Citation: Crowdstrike Hypervisor Jackpotting Pt 2 2021)
Threat actors may also disable or stop service in cloud environments. For example, by leveraging the `DisableAPIServiceAccess` API in AWS, a threat actor may prevent the service from creating service-linked roles on new accounts in the AWS Organization.(Citation: Datadog Security Labs Cloud Persistence 2025)(Citation: AWS DisableAWSServiceAccess)
## Tests
### Test #1 - Stop Application
Adversaries may stop or disable services on a system to render those services unavailable to legitimate users.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| --------------- | ---- | ------------- |
| applicationName | str | `Mail` |
reg query with [Reg](https://attack.mitre.org/software/S0075), dir with [cmd](https://attack.mitre.org/software/S0106), and [Tasklist](https://attack.mitre.org/software/S0057), but other indicators of discovery behavior may be more specific to the type of software or security system the adversary is looking for. It is becoming more common to see macOS malware perform checks for LittleSnitch and KnockKnock software.
Adversaries may also utilize the [Cloud API](https://attack.mitre.org/techniques/T1059/009) to discover cloud-native security software installed on compute infrastructure, such as the AWS CloudWatch agent, Azure VM Agent, and Google Cloud Monitor agent. These agents may collect metrics and logs from the VM, which may be centrally aggregated in a cloud-based monitoring platform.
## Tests
### Test #1 - Check XProtect version
This test checks the version of XProtect, the built-in antivirus in macOS. XCSSET checks whether the version of XProtect is less than 5287.
reload).(Citation: Microsoft Shutdown Oct 2017)(Citation: alert\_TA18\_106A) They may also include shutdown/reboot of a virtual machine via hypervisor / cloud consoles or command line tools.
Shutting down or rebooting systems may disrupt access to computer resources for legitimate users while also impeding incident response/recovery.
Adversaries may also use Windows API functions, such as `InitializeSystemShutdownExW` or `ExitWindowsEx`, to force a system to shut down or reboot.(Citation: CrowdStrike Blog)(Citation: Unit42 Agrius 2023) Alternatively, the `NtRaiseHardError`or `ZwRaiseHardError` Windows API functions with the `ResponseOption` parameter set to `OptionShutdownSystem` may deliver a “blue screen of death” (BSOD) to a system.(Citation: SonicWall)(Citation: NtRaiseHardError)(Citation: NotMe-BSOD) In order to leverage these API functions, an adversary may need to acquire `SeShutdownPrivilege` (e.g., via [Access Token Manipulation](https://attack.mitre.org/techniques/T1134)).(Citation: Unit42 Agrius 2023)
In some cases, the system may not be able to boot again.
Adversaries may attempt to shutdown/reboot a system after impacting it in other ways, such as [Disk Structure Wipe](https://attack.mitre.org/techniques/T1561/002) or [Inhibit System Recovery](https://attack.mitre.org/techniques/T1490), to hasten the intended effects on system availability.(Citation: Talos Nyetya June 2017)(Citation: Talos Olympic Destroyer 2018)
## Tests
### Test #1 - Shutdown system (using System Events)
Shuts down the system using the shutdown command from System Events.
⚠️ TCC Required
SMLoginItemSetEnabled.
Login items installed using the Service Management Framework leverage launchd, are not visible in the System Preferences, and can only be removed by the application that created them.(Citation: Adding Login Items)(Citation: SMLoginItemSetEnabled Schroeder 2013) Login items created using a shared file list are visible in System Preferences, can hide the application when it launches, and are executed through LaunchServices, not launchd, to open applications, documents, or URLs without using Finder.(Citation: Launch Services Apple Developer) Users and applications use login items to configure their user environment to launch commonly used services or applications, such as email, chat, and music applications.
Adversaries can utilize [AppleScript](https://attack.mitre.org/techniques/T1059/002) and [Native API](https://attack.mitre.org/techniques/T1106) calls to create a login item to spawn malicious executables.(Citation: ELC Running at startup) Prior to version 10.5 on macOS, adversaries can add login items by using [AppleScript](https://attack.mitre.org/techniques/T1059/002) to send an Apple events to the “System Events” process, which has an AppleScript dictionary for manipulating login items.(Citation: Login Items AE) Adversaries can use a command such as tell application “System Events” to make login item at end with properties /path/to/executable.(Citation: Startup Items Eclectic)(Citation: hexed osx.dok analysis 2019)(Citation: Add List Remove Login Items Apple Script) This command adds the path of the malicious executable to the login item file list located in \~/Library/Application Support/com.apple.backgroundtaskmanagementagent/backgrounditems.btm.(Citation: Startup Items Eclectic) Adversaries can also use login items to launch executables that can be used to control the victim system remotely or as a means to gain privilege escalation by prompting for user credentials.(Citation: objsee mac malware 2017)(Citation: CheckPoint Dok)(Citation: objsee netwire backdoor 2019)
## Tests
### Test #1 - Create a login item
Creates a new login item that will automatically start when the user logs in.
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| -------- | ---- | ------------------------------------- |
| itemPath | str | `/System/Applications/Calculator.app` |
| isHidden | bool | `False` |
apple.awt.UIElement, which allows for Java applications to prevent the application's icon from appearing in the Dock. A common use for this is when applications run in the system tray, but don't also want to show up in the Dock.
Similarly, on Windows there are a variety of features in scripting languages, such as [PowerShell](https://attack.mitre.org/techniques/T1059/001), Jscript, and [Visual Basic](https://attack.mitre.org/techniques/T1059/005) to make windows hidden. One example of this is powershell.exe -WindowStyle Hidden.(Citation: PowerShell About 2019)
The Windows Registry can also be edited to hide application windows from the current user. For example, by setting the `WindowPosition` subkey in the `HKEY_CURRENT_USER\Console\%SystemRoot%_System32_WindowsPowerShell_v1.0_PowerShell.exe` Registry key to a maximum value, PowerShell windows will open off screen and be hidden.(Citation: Cantoris Computing)
In addition, Windows supports the `CreateDesktop()` API that can create a hidden desktop window with its own corresponding explorer.exe process.(Citation: Hidden VNC)(Citation: Anatomy of an hVNC Attack) All applications running on the hidden desktop window, such as a hidden VNC (hVNC) session,(Citation: Hidden VNC) will be invisible to other desktops windows.
Adversaries may also leverage cmd.exe(Citation: Cybereason - Hidden Malicious Remote Access) as a parent process, and then utilize a LOLBin, such as DeviceCredentialDeployment.exe,(Citation: LOLBAS Project GitHub Device Cred Dep)(Citation: SecureList BlueNoroff Device Cred Dev) to hide windows.
## Tests
### Test #1 - Hide Application Window
Hides the Application window
⚠️ TCC Required
**Input Arguments:**
| Argument | Type | Default Value |
| --------------- | ---- | ------------- |
| applicationName | str | `Terminal` |
HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\Nls\Language or parsing the outputs of Windows API functions GetUserDefaultUILanguage, GetSystemDefaultUILanguage, GetKeyboardLayoutList and GetUserDefaultLangID.(Citation: Darkside Ransomware Cybereason)(Citation: Securelist JSWorm)(Citation: SecureList SynAck Doppelgänging May 2018)
On a macOS or Linux system, adversaries may query locale to retrieve the value of the $LANG environment variable.
## Tests
### Test #1 - Get System Locale
An adversary may gather the system locale settings in order to infer the geographical location of that host.
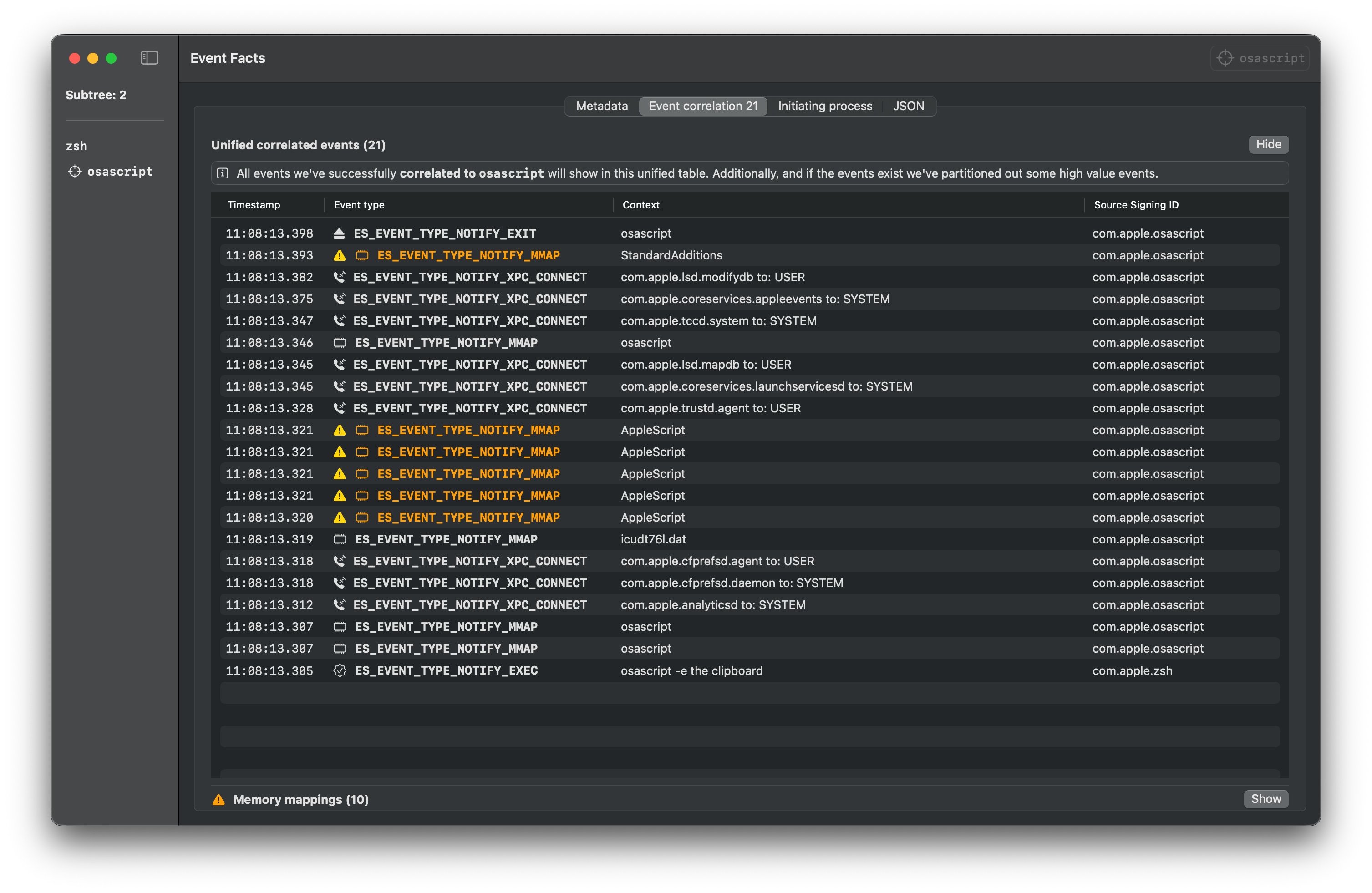 ### Script
Download the script from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with osascript.
```bash
osascript get_clipboard_content_using_applescript_defaults.scpt
```
### Script
Download the script from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with osascript.
```bash
osascript get_clipboard_content_using_applescript_defaults.scpt
```
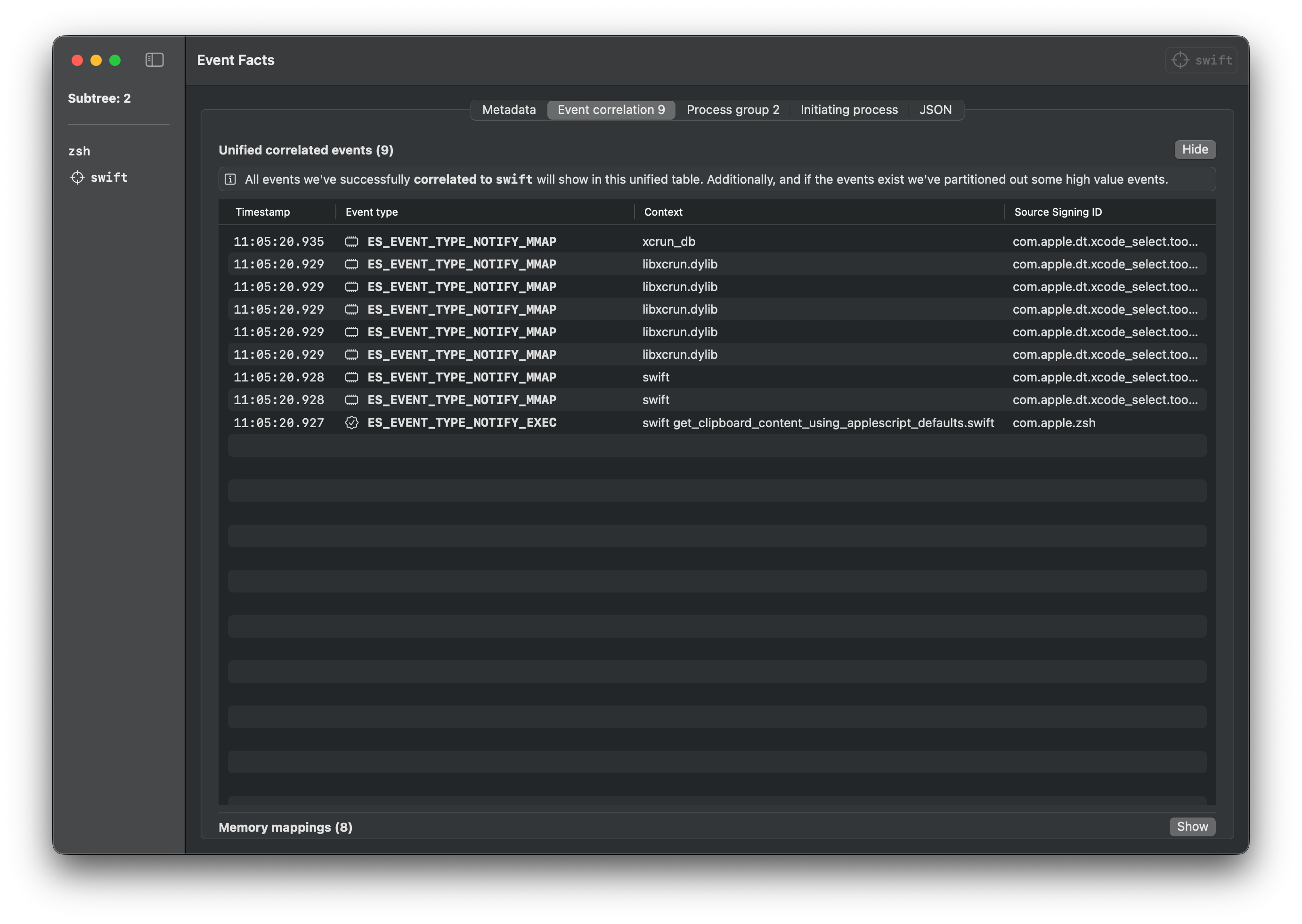
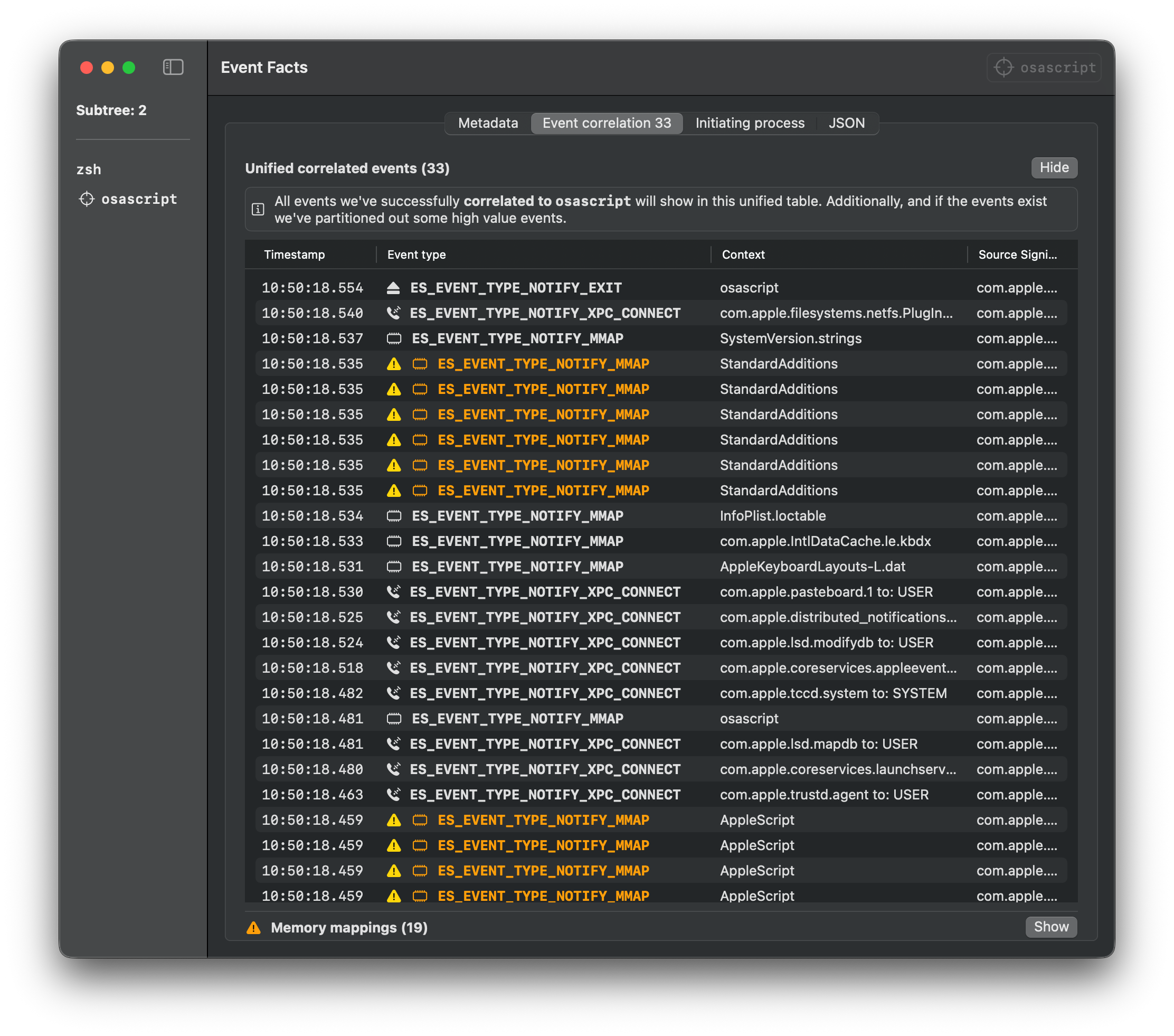 ### Swift
Download the Swift file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with Swift.
Note: You might need to install XCode Developer Tools to run Swift files.
```bash
swift get_clipboard_content_using_applescript_defaults.swift
```
### Swift
Download the Swift file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with Swift.
Note: You might need to install XCode Developer Tools to run Swift files.
```bash
swift get_clipboard_content_using_applescript_defaults.swift
```
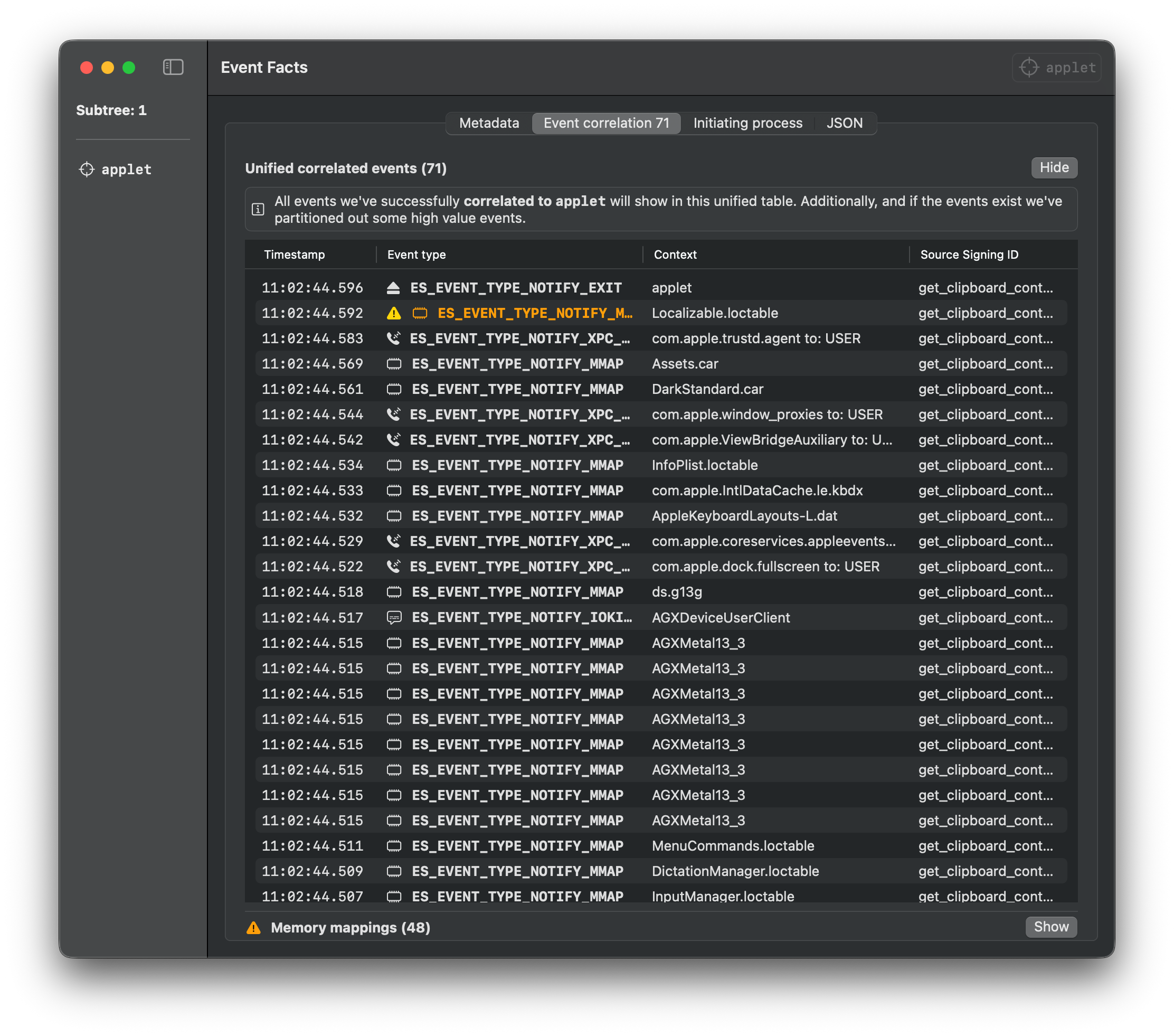
 ### Applet
Download the `.app` file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
open -n get_clipboard_content_using_applescript_defaults.app
```
### Applet
Download the `.app` file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
open -n get_clipboard_content_using_applescript_defaults.app
```
 ### Binary
Download the binary from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
./get_clipboard_content_using_applescript_defaults
```
### Binary
Download the binary from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
./get_clipboard_content_using_applescript_defaults
```
 ### Script
Download the script from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with osascript.
```bash
osascript get_clipboard_content_using_applescript_defaults.scpt
```
### Script
Download the script from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with osascript.
```bash
osascript get_clipboard_content_using_applescript_defaults.scpt
```
 ### Swift
Download the Swift file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with Swift.
Note: You might need to install XCode Developer Tools to run Swift files.
```bash
swift get_clipboard_content_using_applescript_defaults.swift
```
### Swift
Download the Swift file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it with Swift.
Note: You might need to install XCode Developer Tools to run Swift files.
```bash
swift get_clipboard_content_using_applescript_defaults.swift
```
 ### Applet
Download the `.app` file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
open -n get_clipboard_content_using_applescript_defaults.app
```
### Applet
Download the `.app` file from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
open -n get_clipboard_content_using_applescript_defaults.app
```
 ### Binary
Download the binary from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
./get_clipboard_content_using_applescript_defaults
```
### Binary
Download the binary from the [releases page](https://github.com/cyberbuff/loas/releases/latest) and execute it.
```bash
./get_clipboard_content_using_applescript_defaults
```
